LAST UPDATE: 08/05/2025
Hi guys!
So, if you are reading this, I'm dead! Lol kidding.
Seriously now, if you are reading this, you are trying to become a pentester and not a stupid teenager who just wants to run a tool and tell his friends that he is a hacker.
Also, if you are concerned/complaining about the icon size on your desktop, your sound card is not working in Kali Linux, or you are too lazy to read it, go back to your everyday life. You don't have the pentester/hacker soul.
If you are still reading at this point, I already suppose that you have at least the basic knowledge of:
- Linux operation and management
- Windows operation and management
- Some programming language skills (Perl, python, ruby, javascript) also, for web pentest event HTML is required, even if it isn't a programming language
- Basic Network knowledge (TCP/IP, ICMP) /Network services (Proxy, VPN, Samba, AD)
- Protocols like HTTP, FTP, DNS, SSH
- SQL (DDL, DML, and so on), MySQL, SQL Server, Postgres, Oracle.
- NoSQL - MongoDB, and others.
If you don't have these skills, don't try to enter the security world right now, or you will get frustrated. You will need to do a lot of reading before you can start.
Don't think just installing Kali Linux on your machine magically makes you a pentester. It takes time, and to be honest, a lot of time!
If you want to learn Linux, don't start with Kali for the following reasons: http://docs.kali.org/introduction/should-i-use-kali-linux. Basically, these lines: "The fact of the matter is, however, that Kali is a Linux distribution specifically geared towards professional penetration testers and security specialists, and given its unique nature, it is NOT a recommended distribution if you're unfamiliar with Linux or are looking for a general-purpose Linux desktop distribution for development, web design, gaming, etc."
The most important thing is: Know how things work.
I will not discuss the guys who use SET to grab Facebook credentials. I know a lot of "hackers" who can dump entire databases but don't even know how a SELECT or CREATE TABLE statement works, or guys who can take down a server but don't even know what an ICMP type 8 is. I felt sick writing this last sentence…
So, don't be big-headed. Just executing tools does not make you a hacker or pentester. Start your studies correctly.
Don't be a simple stupid script, kiddie. These guys are jokes in the security world. Do you wanna be like these guys? I don't think so.
Another tip: Don't think that everything is free. You must save money to buy books, training, or certifications.
There is a lot of training available on the Internet. I'm saving some time for you:
Here are some books and links to start (I put them in the order that I think is the best way to learn, feel free to choose the best way for you):
https://en.wikipedia.org/wiki/Modern_Operating_Systems
http://iips.icci.edu.iq/images/exam/Computer-Networks---A-Tanenbaum---5th-edition.pdf
http://www.amazon.com/HTTP-Definitive-Guide-Guides/dp/1565925092
https://www.edx.org/course/introduction-linux-linuxfoundationx-lfs101x-0
https://linuxacademy.com/linux
http://linux-training.be/
http://www.htmlandcssbook.com/
https://en.wikiversity.org/wiki/Programming_Logic
https://www.python.org/about/gettingstarted/
https://www.perl.org/books/beginning-perl/
http://www.sqlcourse.com/
https://go.dev/
Now you have at least 6 months of studying ahead and can find more related training. Remember, Google is your friend.
I ALREADY HAVE THE SKILLS (Really? Double check it)
So, if you already have the required skills, there are some excellent references that you can use to get into IT security. Still, first, you should select one area and move to another one after you have mastered it (my recommendation). However, sometimes you have to mix them to get better results. Some security areas (it's not an exhaustive list):
Web Pentesting
Network Pentesting
Mobile Pentesting
SCADA Pentesting
Reverse Engineering
Malware Analysis
Forensics
Security Research
Hardware Security
Exploitation
Hardware Hacking
IoT Pentesting
RedTeaming -> Offensive
BlueTeam -> Defensive
Of course, you can simultaneously share your focus and study more than 1 topic.
If you are still lost, here are some careers you can search for and decide what is more suitable for you:
1. Application Security Administrator – Keep software/apps safe and secure.
2. Artificial Intelligence Security Specialist – Use AI to combat cybercrime.
3. Automotive Security Engineer – Protect cars from cyber intrusions.
4. Blockchain Developer / Engineer – Code the future of secure transactions.
5. Blue Team Member – Design defensive measures / harden operating systems.
6. Bug Bounty Hunter – Freelance hackers find defects and exploits in code.
7. Cybersecurity Scrum Master – Watch over and protect all data.
8. Chief Information Security Officer (CISO) – Head honcho of cybersecurity.
9. Chief Security Officer (CSO) – Head up all physical/info/cyber security.
10. Cloud Security Architect – Secure apps and data in the cloud.
11. Counterespionage analyst – Thwart cyber spies from hostile nation states.
12. Cryptanalyst – Decipher coded messages without a cryptographic key.
13. Cryptographer – Develop systems to encrypt sensitive information.
14. Cyber Insurance Policy Specialist – Consult on cyber risk and liability protection.
15. Cyber Intelligence Specialist – Analyze cyber threats and defend against them.
16. Cyber Operations Specialist – Conduct offensive cyberspace operations.
17. Cybercrime Investigator – Solve crimes conducted in cyberspace.
18. Cybersecurity Hardware Engineer – Develop security for computer hardware.
19. Cybersecurity Lawyer – Attorney focused on info/cyber security and cybercrime.
20. Cybersecurity Software Developer / Engineer – Bake security into applications.
21. Data Privacy Officer – Ensure legal compliance related to data protection.
22. Data Recovery Specialist – Recover hacked data from digital devices.
23. Data Security Analyst – Protect information on computers and networks.
24. Digital Forensics Analyst – Examine data containing evidence of cybercrimes.
25. Disaster Recovery Specialist – Plan for and respond to data and system catastrophes.
26. Ethical / White Hat Hacker – Perform lawful security testing and evaluation.
27. Governance Compliance & Risk (GRC) Manager – Oversee risk management.
28. IIoT (Industrial Internet of Things) Security Specialist – Protect industrial control systems.
29. Incident Responder – First response to cyber intrusions and data breaches.
30. Information Assurance Analyst – Identify risks to information systems.
31. Information Security Analyst – Plan and carry out infosecurity measures.
32. Information Security Manager / Director – Oversee an IT security team(s).
33. Intrusion Detection Analyst – Use security tools to find targeted attacks.
34. IoT (Internet of Things) Security Specialist – Protect network connected devices.
35. IT Security Architect – Implement network and computer security.
36. Malware Analyst – Detect and remediate malicious software.
37. Mobile Security Engineer – Implement security for mobile phones and devices.
38. Network Security Administrator – Secure networks from internal and external threats.
39. Penetration Tester (Pen-Tester) – Perform authorized and simulated cyberattacks.
40. PKI (Public Key Infrastructure) Analyst – Manage the secure transfer of digital information.
41. Red Team Member – Participate in real-world cyberattack simulations.
42. SCADA (Supervisory control and data acquisition) Security Analyst – Secure critical infrastructures.
43. Security Auditor – Conduct audits on an organization’s information systems.
44. Security Awareness Training Specialist – Train employees on cyber threats.
45. Security Operations Center (SOC) Analyst – Coordinate and report on cyber incidents.
46. Security Operations Center (SOC) Manager – Oversee all SOC personnel.
47. Source Code Auditor – Analyze software code to find bugs, defects, and breaches.
48. Threat Hunter – Search networks to detect and isolate advanced threats.
49. Virus Technician – Detect and remediate computer viruses and malware.
50. Vulnerability Assessor – Find exploits in systems and applications.
In these links, you can find more detailed information regarding each carrier:
https://assets.contentstack.io/v3/assets/blt36c2e63521272fdc/blt6b6beaf55a366a55/Poster_Coolest-Careers_v0322.pdf
https://www.sans.org/cybersecurity-careers/20-coolest-cyber-security-careers/
If you are considering using Kali to start your studies, you should visit the link http://docs.kali.org.
This link has a lot of Kali documentation that can help you before you go to the #kali-Linux channel on Freenode or Discord and ask an obvious question. You can also use forums.kali.org. Additionally, as Kali is Debian-based, it is good to check the Debian Linux documentation if you are unfamiliar with this distro.
Some helpful links to start your pentest journey:
Books:
http://www.hackingexposed.com/ - This is a very nice book series that covers a lot of different topics.
This is another very nice book series that covers many topics, like mobile phones, Android phones, cars, and others, not only web applications. Search for it.
http://www.amazon.com/Web-Application-Hackers-Handbook-Exploiting/dp/1118026470
http://www.amazon.com/s/ref=nb_sb_noss_1?url=search-alias%3Dstripbooks&field-keywords=hacker%27s+handbook&rh=n%3A283155%2Ck%3Ahacker%27s+handbook
http://www.amazon.com/SQL-Injection-Attacks-Defense-Second/dp/1597499633/
Red Teaming:
https://www.amazon.de/Red-Team-Succeed-Thinking-Enemy/dp/0465048943
https://www.amazon.de/-/en/Joe-Vest/dp/B083XVG633/ref=pd_lpo_4?pd_rd_i=B083XVG633&psc=1
Also, you can google "Pentest Kali Linux" on Google. There are a lot of related books, just choose one and try.
Links:
One more link in the same style as this post:
https://www.corelan.be/index.php/2015/10/13/how-to-become-a-pentester/
http://www.vulnhub.com - > A lot of vulnerable machines to play with.
http://www.securitytube.com -> A lot of security videos and tutorials.
https://www.cybrary.it -> More security videos
https://pentesterlab.com -> Various pentest exercises
http://hackthebox.eu -> Various pentest exercises
During the last years, the platform Hack The Box (HTB) has grown significantly, becoming a reference in the pentesting, redteaming, and blueteam areas. Recently, I had the opportunity to play in the ProLabs. I can say it was quite a pleasant experience. It helped me to improve and get a lot of skills. I really suggest you play the labs without getting spoilers on the internet. It will definitely make your Google search for kung fu better. Also, the price is very worth it due to the fun you can have. The only problem is that the Labs are shared, so sometimes, it can be challenging to step forward. However, the labs are reset every day. If you get stuck, waiting for the next day is better, as someone may have destroyed the lab or changed some passwords.
I recommend you take VIP access. It's about U$10/month, and it's totally worth it!
I recently finished several ProLabs on Hack The Box, and it is pretty nice to experience hacking in simulated real company scenarios. It's not super cheap, $44/month, but it's worth it. You can read my review here: https://www.linkedin.com/pulse/htb-pro-labs-deep-dive-realistic-penetration-testing-ewerson-w19qf/?trackingId=SdJoCkvvQ3OPwHJ6A3j6aA%3D%3D
https://app.hackingclub.com/
Here you will find extremely nice labs for Red Teaming and Pentesting training in the Portuguese language.
https://en.wikipedia.org/wiki/Hacking:_The_Art_of_Exploitation -> Low Level exploitation
http://www.owasp.org
https://www.owasp.org/index.php/Category:OWASP_WebGoat_Project
https://github.com/enaqx/awesome-pentest
http://worldwideprogramers.blogspot.com.br/2016/07/22-hacking-sites-ctfs-and-wargames-to.html?m=1
Certifications/Training:
https://www.offsec.com
https://www.offsec.com/courses/pen-103/--> FREE TRANING! Register first
https://portswigger.net/web-security --> FREE TRAINING! Register first
http://www.elearn.com -> Moved to https://ine.com/learning/paths -> CyberSecurity
https://www.sans.org
https://www.eccouncil.org/Certification/certified-ethical-hacker
https://courses.zeropointsecurity.co.uk/courses/red-team-ops
https://www.webhacking.com.br/ -> Portuguese language
https://academy.hackthebox.com/preview/certifications
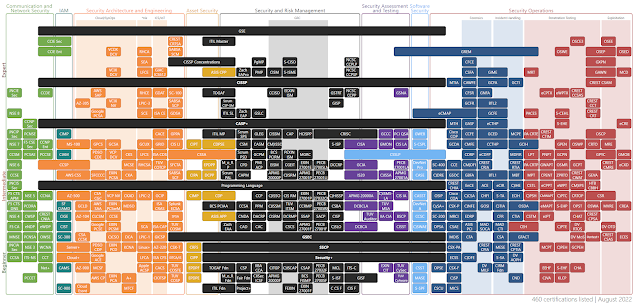
Here is a list of the most expressive certifications in CyberSecurity according to each area:
https://pauljerimy.com/security-certification-roadmap/
Click on the image to enlarge it.
Building a pentest lab:
https://pen-testing.sans.org/blog/2014/02/27/building-a-pen-test-infrastructure-hacking-at-home-on-the-cheap
https://community.rapid7.com/docs/DOC-2196
https://www.cybrary.it/0p3n/tutorial-for-setting-up-a-virtual-penetration-testing-lab-at-your-home/
How To Ask Questions The Smart Way:
http://www.catb.org/esr/faqs/smart-questions.html
Thanks to <Illusional> for the help! \o/