Privilege escalation vulnerabilities are still a major target for attackers looking to breach sensitive systems. Let’s take a look at a specific vertical privilege escalation example, where misconfigured sudo permissions let a low-privileged user run the nmtui tool without needing a password. By using the JSON import feature in Add Team, we can exploit this to escalate our privileges and get ourselves a root shell.
So, there’s a bit of a security issue with how sudo was set up in this case. It lets users with low privileges run nmtui (the Network Manager Text User Interface) as if they were root. Here’s the deal: by playing around with the JSON import feature in the Add Team section of nmtui, it kicks off a vi editor session with root privileges. If someone manages to escape from vi into a shell, they can elevate their permissions all the way to root.
Happy hacking #1337
Step-by-Step Exploitation Guide
Follow these steps to reproduce the vulnerability:
- Use a terminal session where the current user has limited privileges.
- Execute nmtui with sudo.
- sudo nmtui
- Edit a connection.
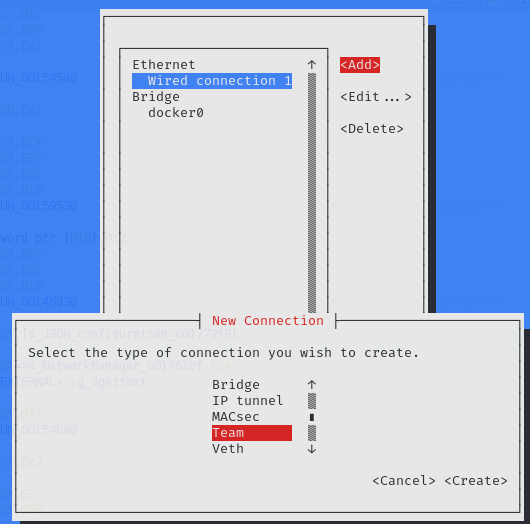
- Select "Add".
- Navigate to the Add option in the nmtui menu.
- Add a Team.
- Proceed by selecting the Add Team option.
- Choose the JSON option.
- In this step, nmtui attempts to import a JSON configuration, opening the vi editor in a root context.
- Escape from vi to a shell.
- Use the following command within vi to spawn a root shell:
- :!/bin/bash
- You are root!
*This behavior is further exploitable if nmtui is configured with the setuid (SUID) bit, allowing any user to execute it with elevated privileges.
Reverse Engineering Insights
The attack was uncovered during a reverse engineering analysis of nmtui using Ghidra, a popular software reverse engineering tool developed by the NSA. The analysis revealed that the JSON import functionality in nmtui invokes the vi editor, creating a security loophole in this case.
As I did not have much time to explore it further, other nmtui features might call the vi.
References
Tools and Techniques:
- Ghidra: Reverse engineering tool used to analyze
nmtui. - Sudo: A powerful tool to allow users to execute commands with elevated privileges.
- SUID: A Unix/Linux file permission that allows users to execute a file with the permissions of the file owner.
Related Escalation Techniques: